How to install a renewed SSL Certificate in Oracle Wallet
The definitive guide to install SSL certificates in Oracle Wallet Manager.
By SMART IT NINJA
Installing SSL certificates is a pretty straightforward task, you just need to download your new signed certificates from the Certification Authority (CA) and install them on your web server of choice ... except if your web server is an Oracle web server that uses something called "Oracle Wallet" to manage them...
Don't panic, this guide will provide you all the necessary steps to install them using operating plain system commands (there's no need for another painful Oracle GUI).
Remember: A wallet is a password-protected container used to store authentication and signing credentials, including private keys, certificates, and trusted certificates needed by SSL.
Oracle provides the orapki utility as command line tool to create and manage all Oracle Wallets since Oracle 10g onwards.
Basically, you will need these elements:
- OpenSSL installed in a machine
- The server's certificate in PEM format
- The server's encrypted private key and it's password
- The CA root and intermediate certificates
With all these elements available, we are ready to dive into this task. Super cool!
14 Steps to SUCCESS
1. Extract the private key from your current wallet
openssl pkcs12 -in ewallet.p12 -passin pass:(wallet password) -out ewallet.txt -nodes
The resulting "ewallet.txt" is a file that contains the unencrypted private key, the certificate and all the Root CA certificates in the wallet. Then the relevant information for the key, and certificate(s) can be copied to separate files to create the individual key and certificate(s).
2. Setup environment variables
export JAVA_HOME=/opt/jdk1.7.0_71 export PATH=$JAVA_HOME/bin:$PATH
Setup your Java runtime accordingly. In this example, we are using JDK 1.7 located in /opt folder.
3. Create a new wallet location
mkdir -p $(LOCATION)/keystores/2019cd $(LOCATION)/keystores/2019
4. Create a temporary OpenSSL Wallet
Extract the private key from "ewallet.txt" and put it into the "privkey.crt" file.
Put the renewed intermediate certificates all together into the "bundle.crt" file.
Put the renewed SSL certificate into the "certificate.crt" file.
Now, let's create an OpenSSL wallet named "ewallet-ossl.p12":
openssl pkcs12 -export -in certificate.crt -inkey privkey.crt -certfile bundle.crt -out ewallet-ossl.p12
5. Export the OpenSSL wallet to a JKS Wallet type
We need to export the current OpenSSL wallet contents to a JKS wallet named "ewallet.jks"
$ORACLE_HOME/oracle_common/bin/orapki wallet pkcs12_to_jks -wallet ./ewallet-ossl.p12 -jksKeyStoreLoc ./ewallet.jks -jksKeyStorepwd (password)
6. Create a definite OpenSSL Wallet
Oracle web servers need an "auto login" wallet, this feature is propietary. Let's create it using the "orapki" utility:
$ORACLE_HOME/oracle_common/bin/orapki wallet create -wallet ./ -auto_login
7. Verify Wallet contents
By default, this process creates a new wallet and populates it with default certificates.
$ORACLE_HOME/oracle_common/bin/orapki wallet display -wallet ./
8. Remove all default certificates
There's no need to have these certificates, let's remove them all from our wallet:
$ORACLE_HOME/oracle_common/bin/orapki wallet remove -trusted_cert_all -wallet ./
9. Verify that your wallet is empty
Let's verify the wallet contents again:
$ORACLE_HOME/oracle_common/bin/orapki wallet display -wallet ./
10. Import JKS content
Import the exported JKS content into our new wallet:
ORACLE_HOME/oracle_common/bin/orapki wallet jks_to_pkcs12 -wallet ./ -pwd (password) -keystore ewallet.jks -jkspwd (password)
11. Validiting the new content
At this stage, all the renewed certificates should be displayed as our wallet content:
$ORACLE_HOME/oracle_common/bin/orapki wallet display -wallet ./
13. Update Oracle Web Server SSL configuration file
Now, we are ready to update our wallet location in SSLWallet directive
14. Restart the OHS web server
Restart the OHS web server, enter any given URL that points back to your web server and verify that the new SSL certificate is being served as expected.
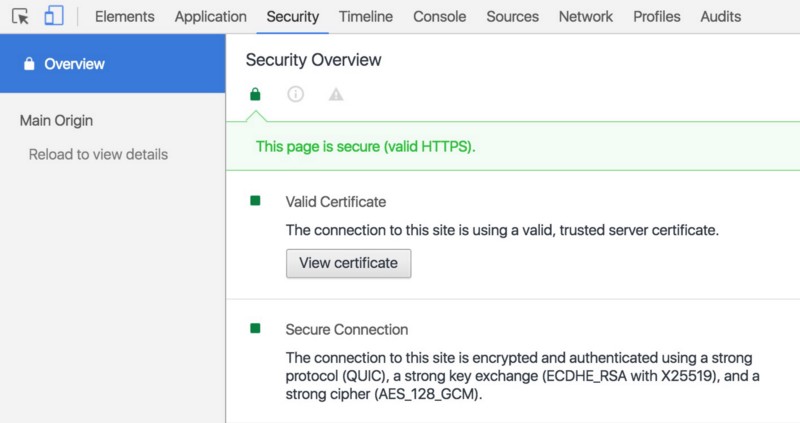
And that's all folks!
Need help? Don't hesitate and reach out to me!
There are a number of ways we can work together and I look forward to exploring the possibilities with you.

Enrique Garibay
MLMLEADS.COM
"Daniel was quick, efficient and thorough with his work. Thanks!"

SHAWN WHITAKER
REALTYISP.COM
"Daniel did a great job and plan to use him again"